High Level Overview
Authentication against an Identity Provider
(1) When a user logs on to the XplicitTrust Agent on a client, they are first redirected to the associated the associated Identity Provider for the tenant.
(2) After the user is authenticated, the identity provider notifies the XplicitTrust Controller and establishes a control connection between the XplicitTrust Agent and the XplicitTrust and the XplicitTrust Controller.
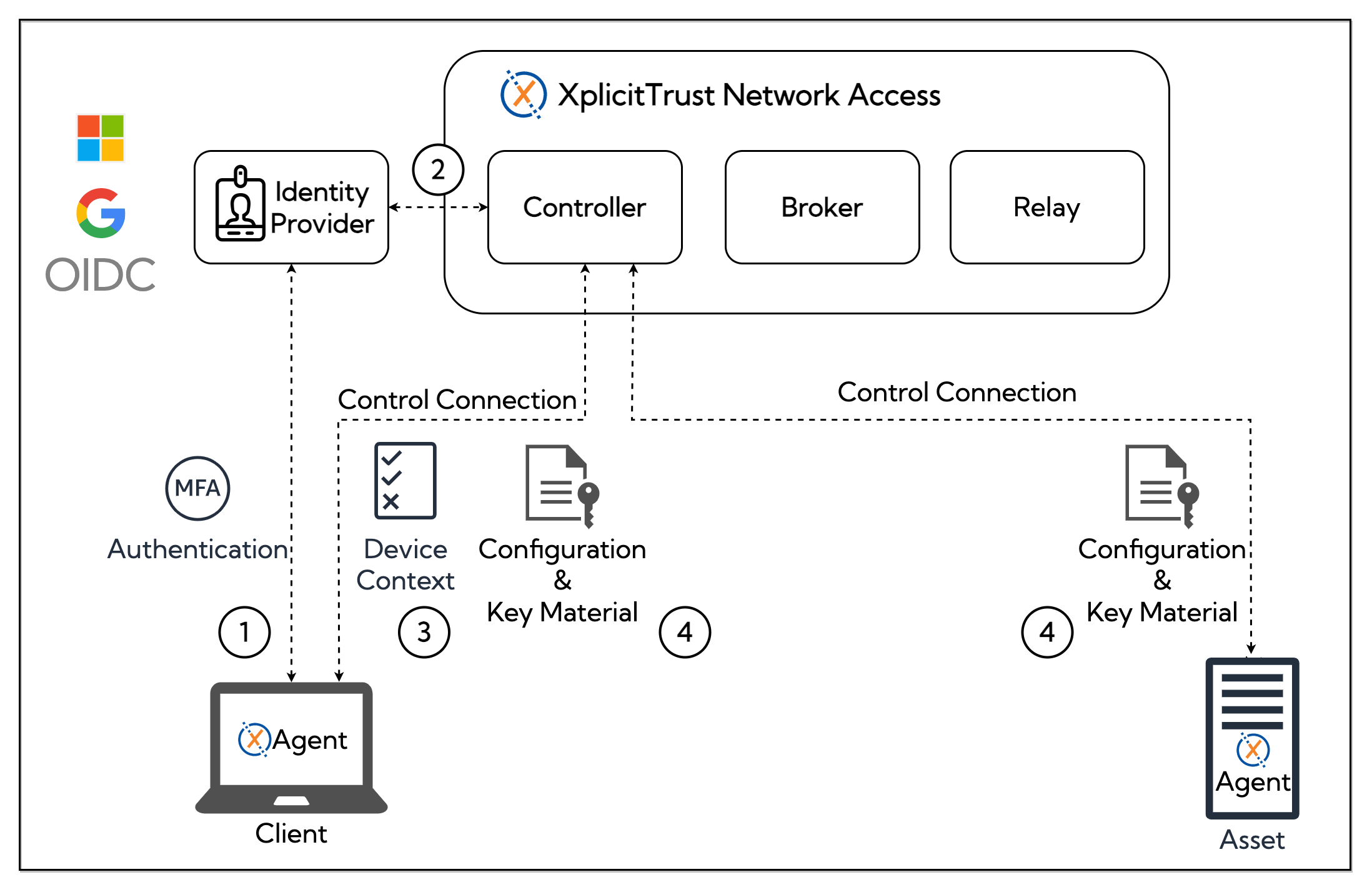
XplicitTrust controller computes access permissions
(3) The XplicitTrust agent sends information about the device context to the controller. For example
- Operating System
- Operating system version
- Geographic location
- Domain membership
- Security posture
Based on the user identity, it's group memberships in the identity provider's directory service, and the device context attributes, the XplicitTrust controller calculates what assets the user is authorized to is authorized to access on that client.
Configuration and Public Key Material is Deployed
(4) The configuration and public key material is deployed to the client and the assets it can access. The private keys are generated on the clients and assets and never leave the device.
A connection is established
(5) Both peers first connect through the XplicitTrust relay service. The connection is encrypted end-to-end.
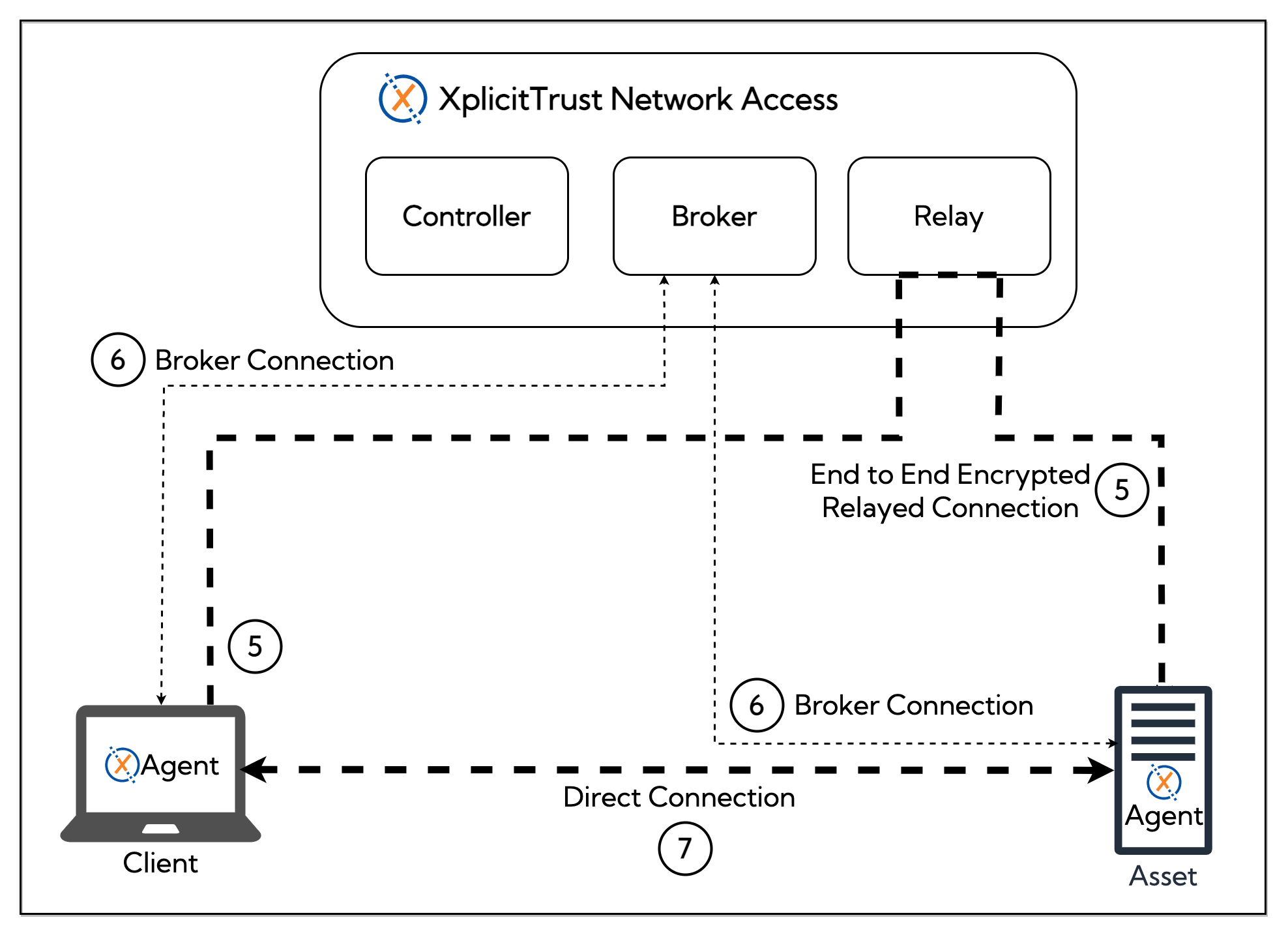
Connection Classification and Optimization
(6) All clients and assets connect to the XplicitTrust broker service. The broker classifies the connection and orchestrates attempts to find optimal direct connections between peers.
Possible connections between peers fall into the following hierarchy:
- Relayed connection
- Direct connection
- Direct, local connection
(7) If a direct connection is possible, the peers switch and send traffic directly.