Quick Start Guide
This document will help you to:
- Sign Up for an XplicitTrust account
- Install the XplicitTrust Agent on at least one asset and one or more clients
- Define a Policy to grant access to assets
Choosing an Identity Provider
Before you sign up you have to decide which Identity Provider you want to use. Most organizations have Microsoft Entra ID, while some are opting for European services like AuthN by IDEE or Bare.ID. For more information and a comparison of the different options please refer to Identity Providers.
For this quick start guide, we'll use Microsoft Entra ID.
Creating an account with XplicitTrust (Signing Up)
-
You need an Microsoft Entra ID user account with one of the following admin privileges:
- Global Administrator
- Application Administrator
- Cloud Application Administrator
-
Let's sign up for XplicitTrust admin portal account (if you don't have one already):
-
Click the Signup button.
-
Follow the Microsoft Login process.
-
When presented with the Microsoft "Permissions Requested" screen, please check the "Consent on behalf of your organization" box (very important) and click Accept:
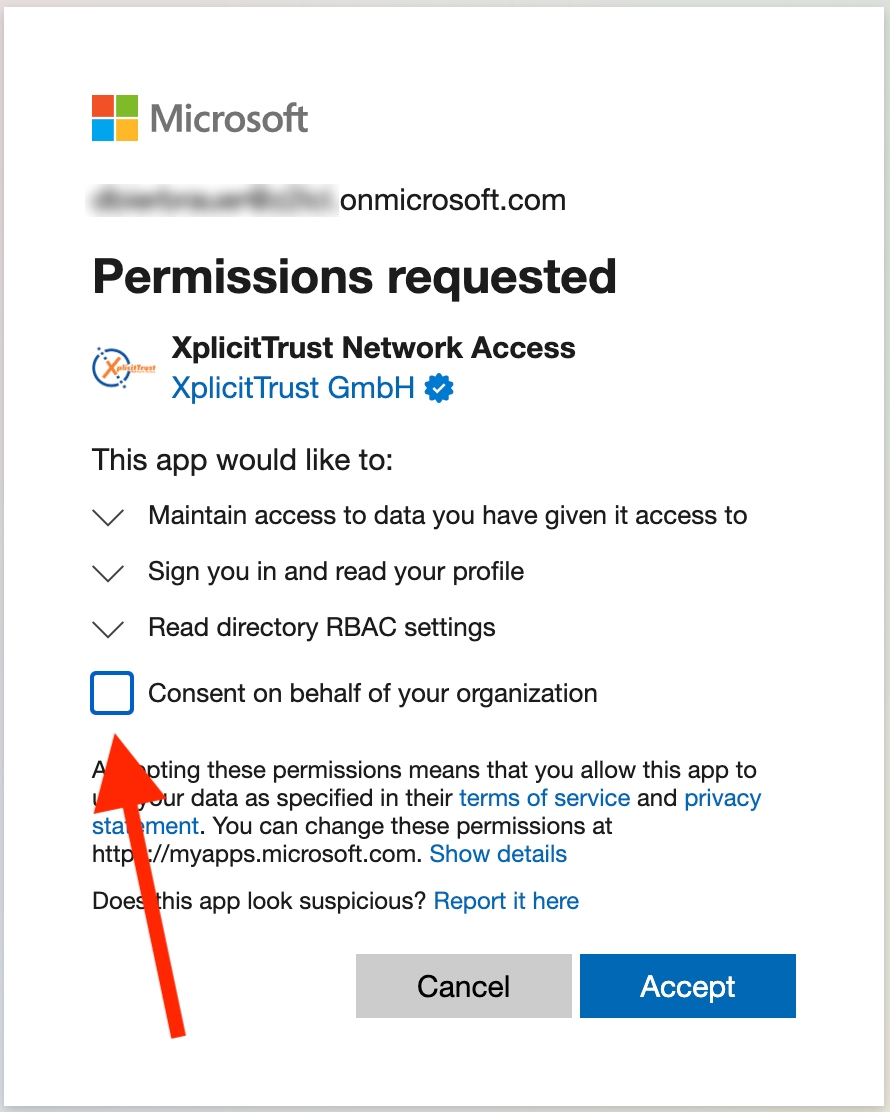
-
Next, the process will ask you to sign in for a second time, and present you with a second Microsoft "Permissions Requested" screen. Please click Accept here also:
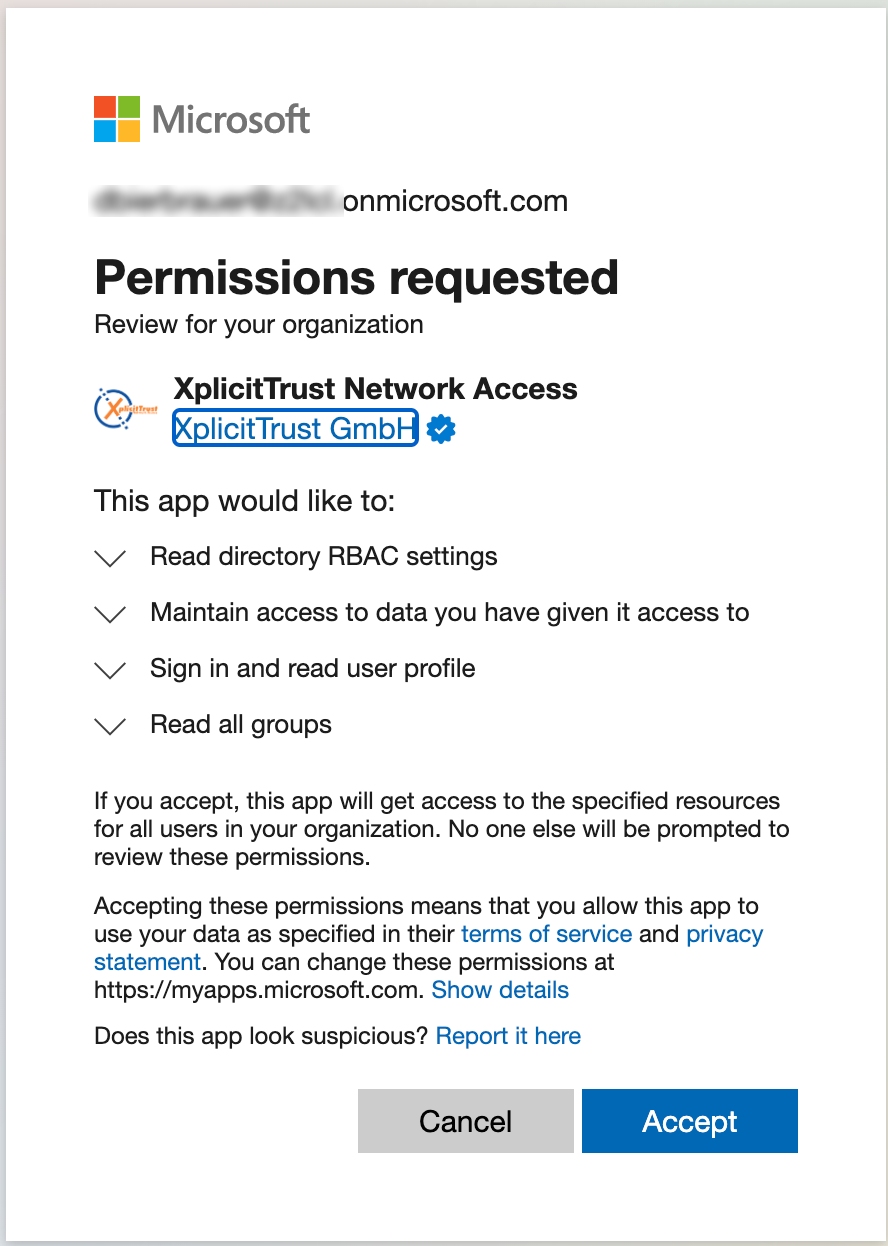
-
You are now signed in to the XplicitTrust admin portal:
https://console.xplicittrust.com/
Assets vs. Clients
With XplicitTrust you can connect any number of devices with each other.
Before connecting a device, you need to decide whether the device will function as a client or as an asset (or -for advanced users- as a virtual asset):
-
Clients:
Devices that will access services on other devices. Typically, regular users' computers or laptops will be set up as clients. -
Assets:
Devices that can be accessed by other devices and provide services like SSH, HTTPS, RDP, etc. Typically, servers will be set up as assets. Additionally, assets can also be peered, to access one another. -
Virtual Assets (only for advanced users):
Like regular assets, but for devices on which you don't want to or can't install our agent. Examples are printers, network cameras, some file sharing servers, unpatchabe legacy systems, etc. These devices can be accessed via another asset that needs to be in the same network (the "providing asset", which needs to be a Linux/Raspberry Pi system).
Get Your First Devices Connected
To get you started and see the system in action, we recommend setting up one device as a client, and one device as an asset.
-
Set up one device as client:
-
Set up one device as an asset:
For Linux click here, or
for Windows click here, or
for Mac click here. -
Now you can access the asset device from the client device:
-
Click on the client icon in the system tray (Windows) or in the status bar (Mac) to see "Available Assets" listed:
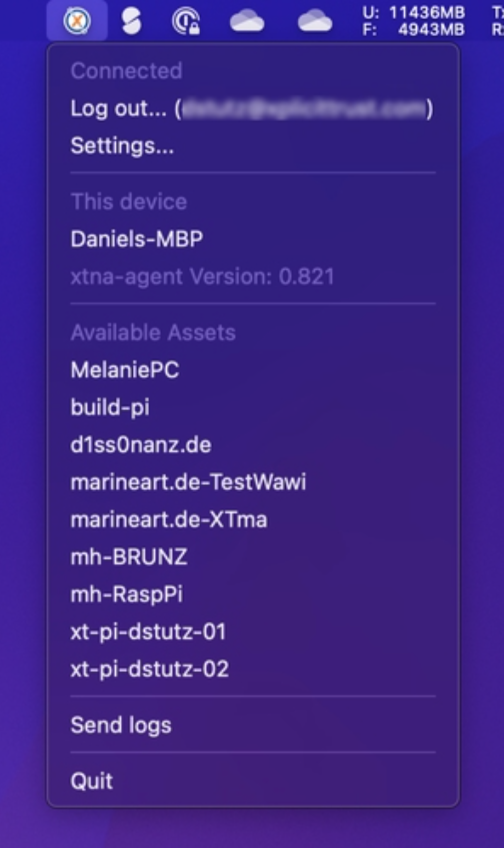
-
Clicking on an asset in the list brings up a window with additional information.
-
You can access your asset from the client by either using its hostname (shown in the menu under "Available Assets"), or by using its Tunnel IP (starts with 100.100....).
-
Policies in XplicitTrust
-
By default, we have a "Deny All" policy set up for all assets.
-
This means if you create a new asset, no client and no asset has access to the new asset.
-
There are two ways to grant access to an asset:
-
By creating a policy (or updating an existing one) at https://console.xplicittrust.com/#/policies/info
-
By using the -default-policy command line flag during asset installation, which will assign the asset to the "Default Policy".
# Asset will be registered and added to the "Default Policy": sudo /usr/sbin/xtna-util -user <your_email_address> -default-policySpecial Case: Allowing Asset Access to another Asset
We currently have a special case (temporarily): Granting one or more asset(s) access to an asset (rather than granting clients access, as outlined above).
This is possible, but does not happen on the regular policy page. Instead, you need to go the Asset Policy page:
-